Our mission-driven solutions guard against data breaches while making sure operations continue to run smoothly.
Cherokee Federal's cybersecurity and privacy solutions strategically design innovative IT solutions to mitigate risk, providing federal departments and agencies (D&As) peace of mind in the ever-evolving digital landscape. We accelerate network transformation by engineering targeted, flexible solutions that align with organizational objectives and improve outcomes.
Let's TalkCyber Solutions
We deliver cybersecurity and privacy (CS&P) approaches, methodologies and best practices that address key concerns such as interoperability, usability and privacy. We do not engineer off-the-shelf solutions. We adapt each one to meet the needs of our customers and equip them with the tools needed to secure networks today while evolving to defeat the cyber threats of tomorrow.
In 2023, Cherokee Federal acquired Criterion Systems, a leading cybersecurity and IT services company. Founded in 2005 and headquartered outside Washington, D.C. in Vienna, Va., Criterion serves as a strategic partner and trusted prime contractor for many of the nation’s most mission-critical environments across more than a dozen agencies. Today, Cherokee Federal customers benefit from Criterion’s deep experience and intellectual capital.
Capabilities
-
Navigating the complex landscape of cybersecurity regulations and best practices demands expertise and finesse. Cherokee Federal’s IT experts deliver robust governance frameworks and continuous program management support that keep federal departments and agencies protected and compliant. Our Cybersecurity Operations Maturity Model (COMM) and supporting tool, CyberScale®, provides a structured process to manage and optimize the efficiency and effectiveness of organizational CS&P programs. With COMM, we ensure customers are equipped to perform with excellence at every phase and milestone while safeguarding your data with confidence.
Capabilities
• CS&P training support
• CyberScale® Cybersecurity & Privacy Review Support
• Cybersecurity & Privacy (CS&P) Program Execution, Policy, & Governance
• Enterprise Vulnerability Management & Mitigation Program Support
• Risk Management Framework Support
Solutions
• Cybersecurity & Privacy Center of Excellence
• Risk Management Framework (RMF) approach -
At Cherokee Federal, we explore the impact of the technological, social and economic trends that are driving change and collaborate with our innovation partners to evaluate relevant emerging commercial and government cybersecurity platforms. We develop solutions that secure and defend our customers’ operating environments, while meeting today’s cybersecurity challenges and anticipating tomorrow’s.
Capabilities
• CS&P Product Research, Evaluation, Testing, & Secure Configuration Support
• Cyber Defense Technology / Information System Protection Support
• Cybersecurity Infrastructure O&M
• Enterprise & Security Architecture Support
• ISSE / Security Control Support
• IT & Cybersecurity Integration
• Secure IT Development, Design, & Implementation SupportSolutions
• Zero Trust Approach
-
Cherokee Federal helps government agencies secure and defend their computer networks through reliable, trustworthy cybersecurity operations centers (CSOCs). We employ a combination of advanced technologies, proven methodologies and diverse cyber expertise to stay ahead of ever-evolving cyber threats. Cherokee Federal provides flexible and self-adjusting CSOC teams to respond to events and continuously adapt and learn as information is shared. We train our engineers and analysts to meet and exceed high standards.
We design and build operation centers based on our customers’ individual needs, operational structure, and applicable governing policies. Our focus spans infrastructure protection, privacy protection and industrial control systems, with the goal of creating a comprehensive security framework that safeguards vital national interests.
Capabilities
• Critical Infrastructure Planning & Program Support
• Industrial Control Systems (ICS) Support
• National Security Systems & Intelligence Community Cybersecurity Support
• Privacy Protection Support
• Security Operations Center Support
• Streamlining OperationsSolutions
• Cyber Hunt Approach
• Cyber Operations Maturity Model
• Cybersecurity Operations Centers (CSOCs)
• Incident Response Approach -
Cherokee Federal’s IT experts have developed a reliable, effective approach to help federal agencies protect mission-critical systems and sensitive data against evolving digital threats. We integrate these cybersecurity measures seamlessly into enterprise architectures and software development life cycle processes.
Making well-informed security authorization decisions throughout the life cycle of information systems can be challenging. We provide the expertise and solutions needed to make these decisions with confidence, comply with evolving regulations and keep systems secure.
Because no two agencies are alike, we offer customized, flexible solutions that allow customers to prioritize security controls and monitoring based on specific values of each system, organizational risk tolerance and the threat landscape. Our cybersecurity and privacy (CS&P) professionals effectively leverage the dynamic nature of the risk management framework (RMF) to enhance our customer’s ability to manage risk and protect national infrastructure more effectively.
Capabilities
• Audit support
• Command Cyber Readiness Inspection (CCRI) Support
• Cyber Supply Chain Risk Management (SCRM) Support
• Cybersecurity Service Provider (CSSP) Support
• Information Systems Continuous Monitoring (ISCM) Support
• Risk management & Risk Assessment Support
• Security Assessment and Authorization (SA&A) / RMF Support
• Site Assistance Visits (SAVs)
Solutions• Cyber Operations reviews
• High Value Asset (HVA) Assessment Approach
• Penetration Testing Approach
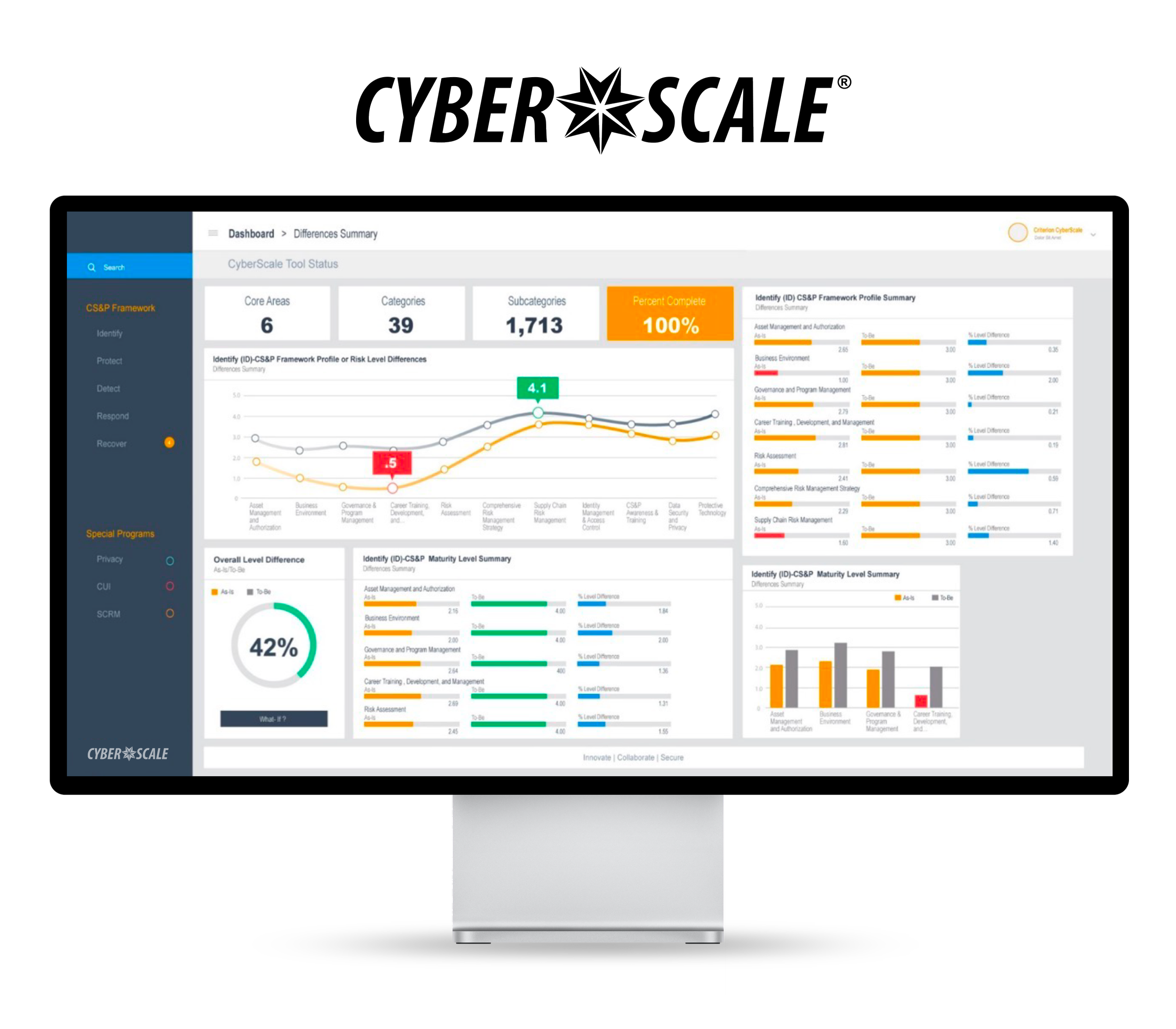
Optimize Your Cybersecurity Program with Cherokee Federal's CyberScale
Cherokee Federal's CyberScale® is a structured framework designed to enhance the efficiency and effectiveness of your Cybersecurity & Privacy (CS&P) programs. It helps federal Departments and Agencies assess their current state, identify improvement priorities, and implement a flexible roadmap for continuous improvement. By aligning with federal standards such as FISMA, NIST, OMB, DHS, and OIG, CyberScale®measures program maturity and defines an optimized target state tailored to your organization's mission and risk appetite.
Our approach delivers a strategic roadmap with clear milestones, corrective action plans, and measurable performance metrics. With CyberScale®, your organization gains a forward-thinking, adaptable framework to optimize CS&P operations, align with compliance requirements, and achieve meaningful, long-term results.
With Cherokee Federal’s CyberScale®, you gain: A forward-thinking, adaptable approach to CS&P optimization. Clear performance metrics for success. A roadmap to align your program with federal compliance and your unique risk management strategy. Let Cherokee Federal's CyberScale®help you create a resilient, efficient, and forward-looking CS&P program.
Rapid Acquisition Contracting Tribal 8(a) Direct Award
Cherokee Federal understands the burdens many federal agencies encounter when facing unprecedented disruptions to procurement strategies and timelines. Our team of companies offers unique acquisition solutions that give government decision-makers the flexibility necessary to take on these unprecedented challenges. The Tribal 8(a) program includes a sole-source procurement method that permits the selection of a qualified contractor of choice. Unlike traditional 8(a)s, there is no dollar threshold limitation on sole-source contracts awarded to a tribally owned 8(a) (regulation: 13 CFR 124.506).
Contracting Benefits Include:
• Civilian agencies, direct award ceiling without justification & approval (J&A) $25 million
• DoD agencies, direct award ceiling without J&A $100 million
• Unlimited direct award ability with J&A
• Direct awards to tribal 8(a)s cannot be protested
Join our team. We move missions that matter forward.
Our mission is to protect the present while preparing for a smarter future. We are looking for individuals that share our vision.
Leadership
Our cybersecurity and privacy solutions are led by Bob Heckman, an expert with significant experience designing and implementing large-scale privacy programs that protect critical digital assets for federal agencies. Contact us today to put the power of Cherokee Federal to work for you.
Bob Heckman
Vice President, Cyber Security & Privacy Solutions Lead
bob.heckman@cherokee-federal.com